Wallet Integration Guide
This guide will walk you through how to integrate the Blowfish API into your wallet. First, we'll cover the areas where wallets get the most benefit from Blowfish. Second, we'll share the tools that make integration fast & easy. Let's get started.
Where to Integrate Blowfish
There are three places to integrate Blowfish to get the most benefit:
- Your transaction approval screen
- Your message signing screen
- Your dApp browser or current domain blocklist
Let's dive into what each of these look like.
1) Transaction scanning & simulation
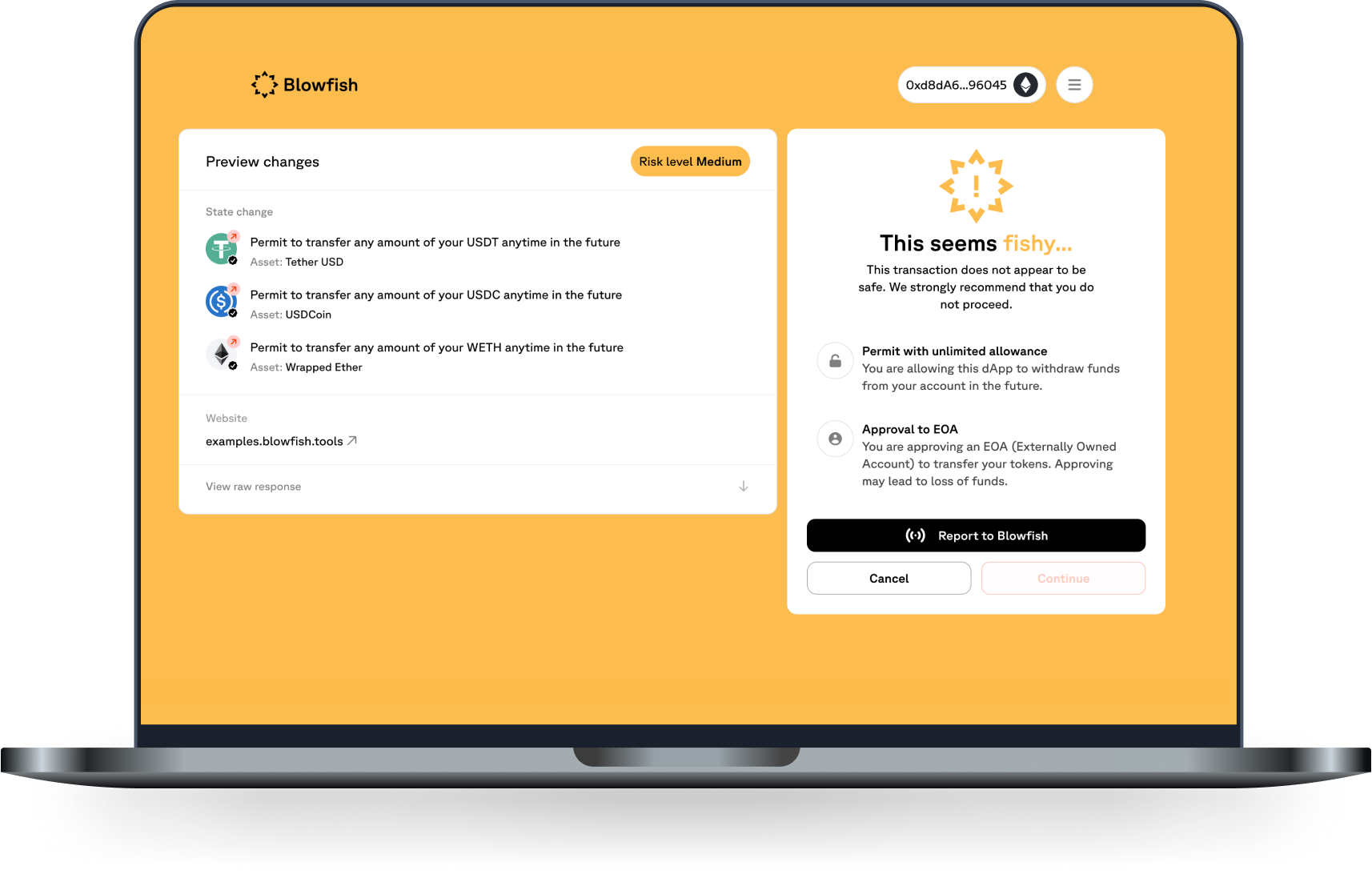
Before a user approves a blockchain transaction, it is paramount to show them an up-to-date preview of how executing this transaction will impact their crypto assets. In order to ensure the preview us fresh, you will want to re-request the simulation results in the background every 5 seconds. In addition, it's important to alert them if the transaction is dangerous with an automated warning. This is what the Blowfish transactions endpoints allow you to do (Solana, Ethereum).

In addition to warnings and simulation results, the API response also returns a suggested action. The recommended action might be to show the user a block screen instead of the approval screen. This is reserved for cases where the user is interacting with a known malicious entity. When the "BLOCK" action is returned, it would be ideal to show the user a block screen.

It is recommended to still allow the user to bypass the block screen and proceed with signing. There are cases where the user knows best & wants to assume the risks.
For integration, we recommend using the Blowfish API client shared later in this guide.
2) Message scanning
Signing certain messages can lead to users losing funds. Sometimes the message itself is a transaction. Other times, it represents an off-chain DEX order that once submitted on-chain has the authority to transfer a users funds. Because of this, it would be best to evaluate a message before showing a message signing interface to your user. The Blowfish API can help you conduct this evaluation. You can check out the Messages endpoint here: Message Endpoint
For integration, we recommend using the Blowfish API client shared later in this guide.
3) Domain scanning & Blocklist
When a user visits a dApp via your wallet's dApp browser or while using your browser extension, you now have the ability to check whether the dApp is dangerous. There are two ways to implement this.
-
The Blowfish domains endpoint allows you to check if a domain is on a trusted blocklist (e.g., Metamask, Phishfort, ScamSniffer, etc.) or if it's been flagged as malicious by Blowfish's detection engine. If a domain is found to be dangerous, the API will return a high risk score and you can warn the user visiting the site. Check out the domains endpoint documentation for more information.
-
The Blowfish blocklist endpoint allows you to download a snapshot of all blocked domains in order to check each domain that a user visits against a local blocklist, preserving each user's browsing history. This integration takes a little more engineering work, but is fast & private once integrated. Explore our blocklist NPM package which offers support for web applications, browser extensions, React Native, and Node.js or check out the blocklist endpoint documentation for more information.
For integration of either of these domain-blocking tools, we recommend using the Blowfish API client shared later in this guide.
How to Integrate Blowfish
Blowfish's Javascript / Typescript API Client
There's a full API client available here: Blowfish API Client that will help you implement transaction & message scanning, domain scanning, and many other features across EVM & Solana. We highly recommend using it to integrate as it will make both integration & maintenance easy & fast.
Other programming languages
In order to use the Blowfish API with other programming languages, please integrate with our HTTP endpoints directly. We would like to support more languages in the future, so please let us know what type of language support you would like by letting our team know directly.
Optional proxy server
Some wallets wish to proxy API requests to third-party APIs over a proxy server. This is also possible when interacting with Blowfish and we highly encourage it. The benefits of doing so are two-fold:
- You do not expose your Blowfish API key to clients and only append it to the requests proxied
- You can prevent your user's IP addresses from being sent to Blowfish. We do not store or use the IP addresses attached to API requests but could access this information if you don't use a proxy.
We highly recommend making the proxy a clear pass-through proxy that does not modify the request or response in any way. Check out our sample proxy server here that implements the necessary functionality: Sample Proxy Server
Updated 11 months ago
